What is SAML?
Security Assertion Markup Language (SAML, pronounced SAM-el) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. In non-jargon speak, SAML SSO (Single Sign On) lets your users login to Sonderplan (the service provider) with third party identity providers, such as Google Workspace, Okta, Azure Active Directory and Onelogin.SAML SSO is available to all of our customers and we recommend implementing it to boost your companies security posture
Enabling SAML SSO
To enable SAML SSO go to Admin -> System Settings, expand the SAML Sign On (SSO) Settings accordion and then change the Enable SAML SSO option to Enabled.Identity Provider Details
These settings will be supplied via your Identity Provider, eg. Google Workspace, Microsoft Azure Active Directory etc. Please copy and paste them into the relevant fields and refer to the guides further down on how to configure SAML within your Identity Provider.Identity Provider Name
This field will be displayed on the SSO sign in button on the login screen.IDP Entity ID / Issuer URL
Identity Provider Issuer Entity ID, often a URL, eg. http://okta.com/Eksj7Hhsk24klljsdIDP Login URL / SSO Endpoint
The URL that Sonderplan will call to request a user login from the Identity ProviderIDP Logout URL / SLO Endpoint
The URL that Sonderplan will call to request a user logout to the Identity ProviderIDP X.509 Certificate
The authentication certificate issued by your Identity ProviderConfiguration Guides
These guides cover the most common identity providers that our customers use, however if you’re running into issues or need help with configuring a different provider, please reach out to our support team.Google Workspace
To configure Sonderplan SAML SSO with Google Workspace, please expand and follow the instructions in each section:1. Create new Google Workspace SAML app
1. Create new Google Workspace SAML app
- Login to the Google Workspace Admin Console and navigate to Apps -> Web and mobile apps.
- Click Add app -> Add custom SAML app
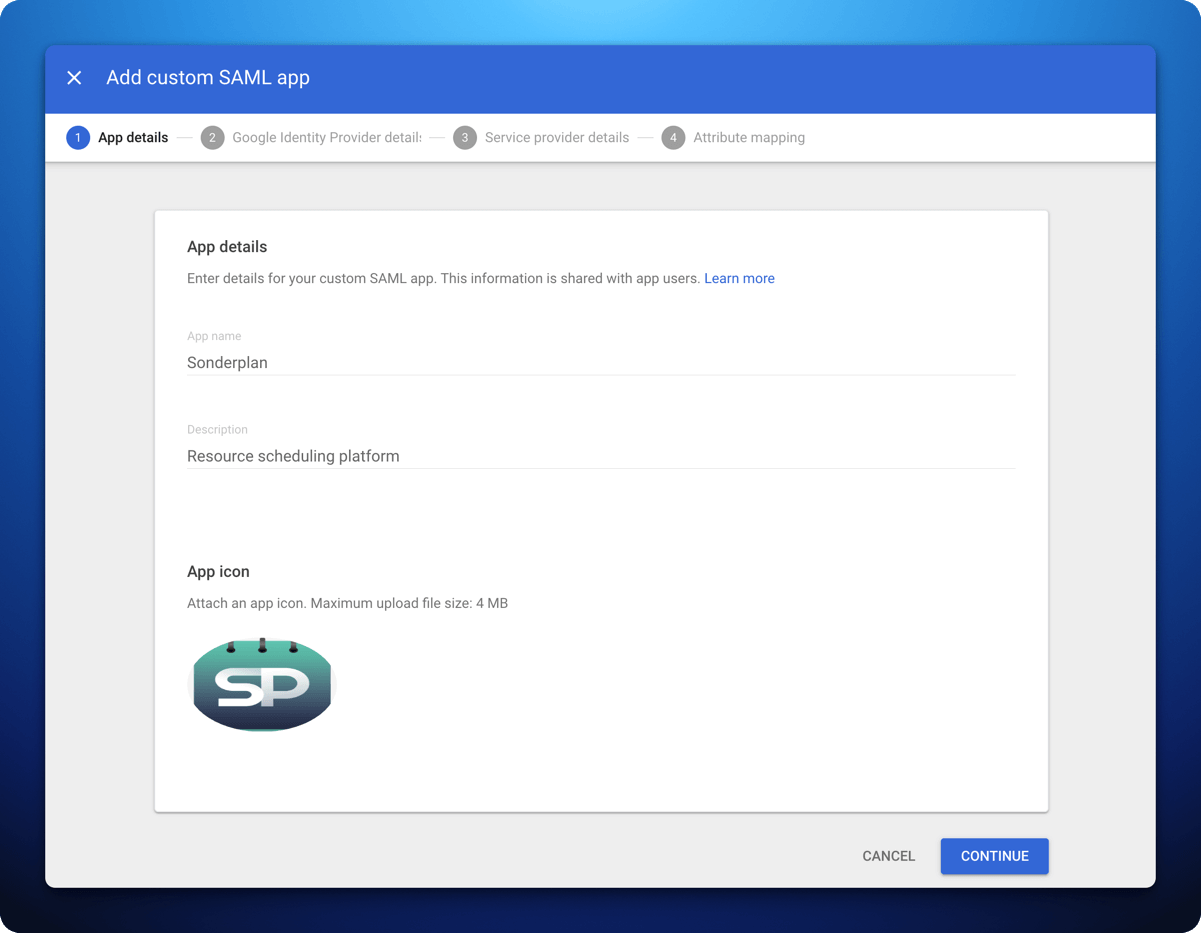
- In App details enter Sonderplan as the App name, with a Description of Resource scheduling platform
- Upload the App Icon which you can save from here:

- Click Continue
2. Copy Google Workspace details into Sonderplan
2. Copy Google Workspace details into Sonderplan
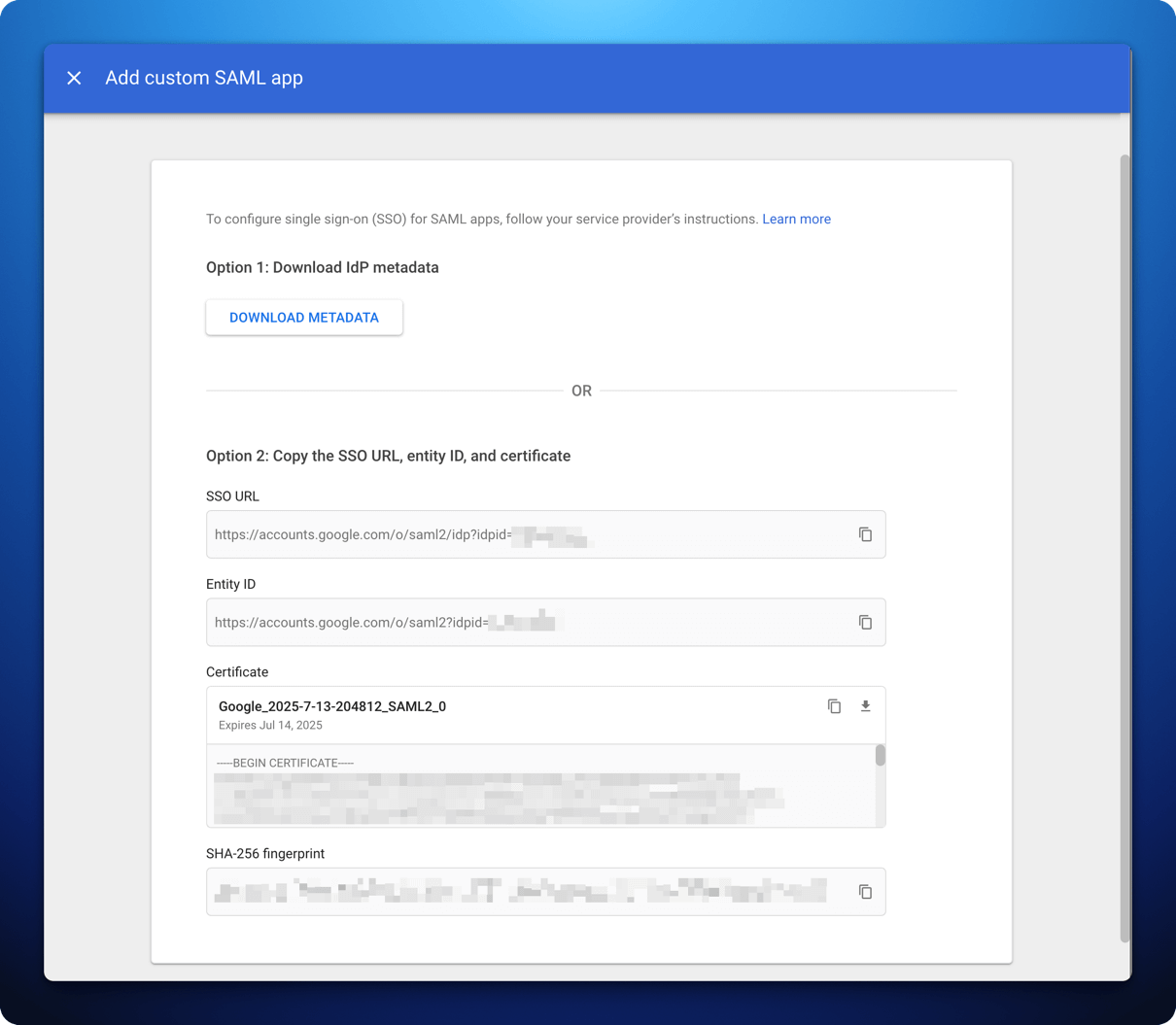
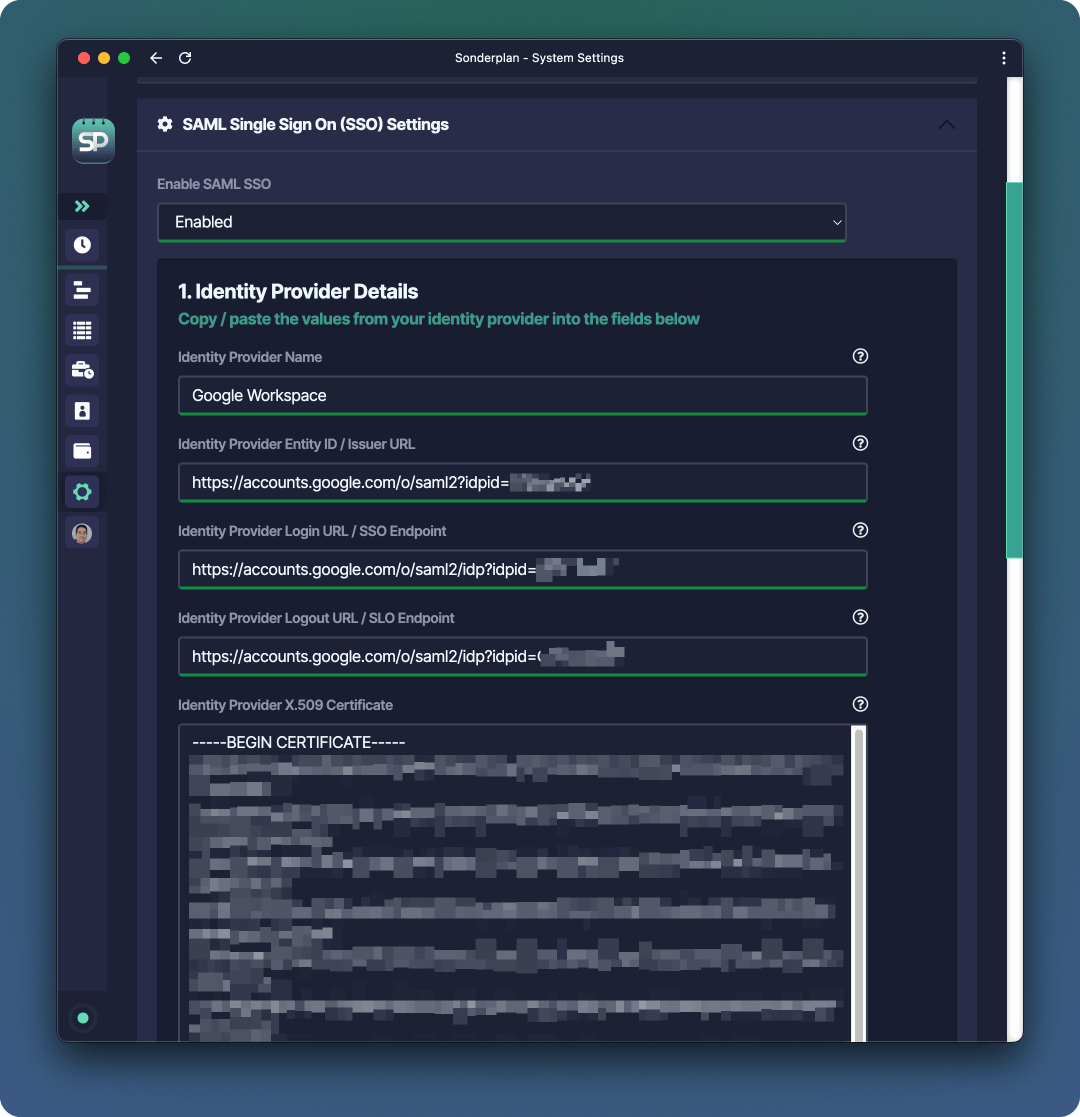
- In Sonderplan, head over to Admin -> System Settings and expand the SAML Single Sign On (SSO) settings panel
- Enable SAML SSO and enter Google Workspace as the Identity Provider Name
- Copy the SSO URL from Google Workspace to -> Identity Provider Login URL / SSO Endpoint AND Identity Provider Logout URL / SLO Endpoint in Sonderplan
- Copy the Entity ID from Google Workspace to -> Identity Provider Entity ID / Issuer URL in Sonderplan
- Copy the Certificate from Google Workspace to -> Identity Provider X.509 Certificate in Sonderplan
- Click Save Changes in the top right corner of Sonderplan
- In Google Workspace, click Continue
3. Enter Service Provider details into Google Workspace
3. Enter Service Provider details into Google Workspace
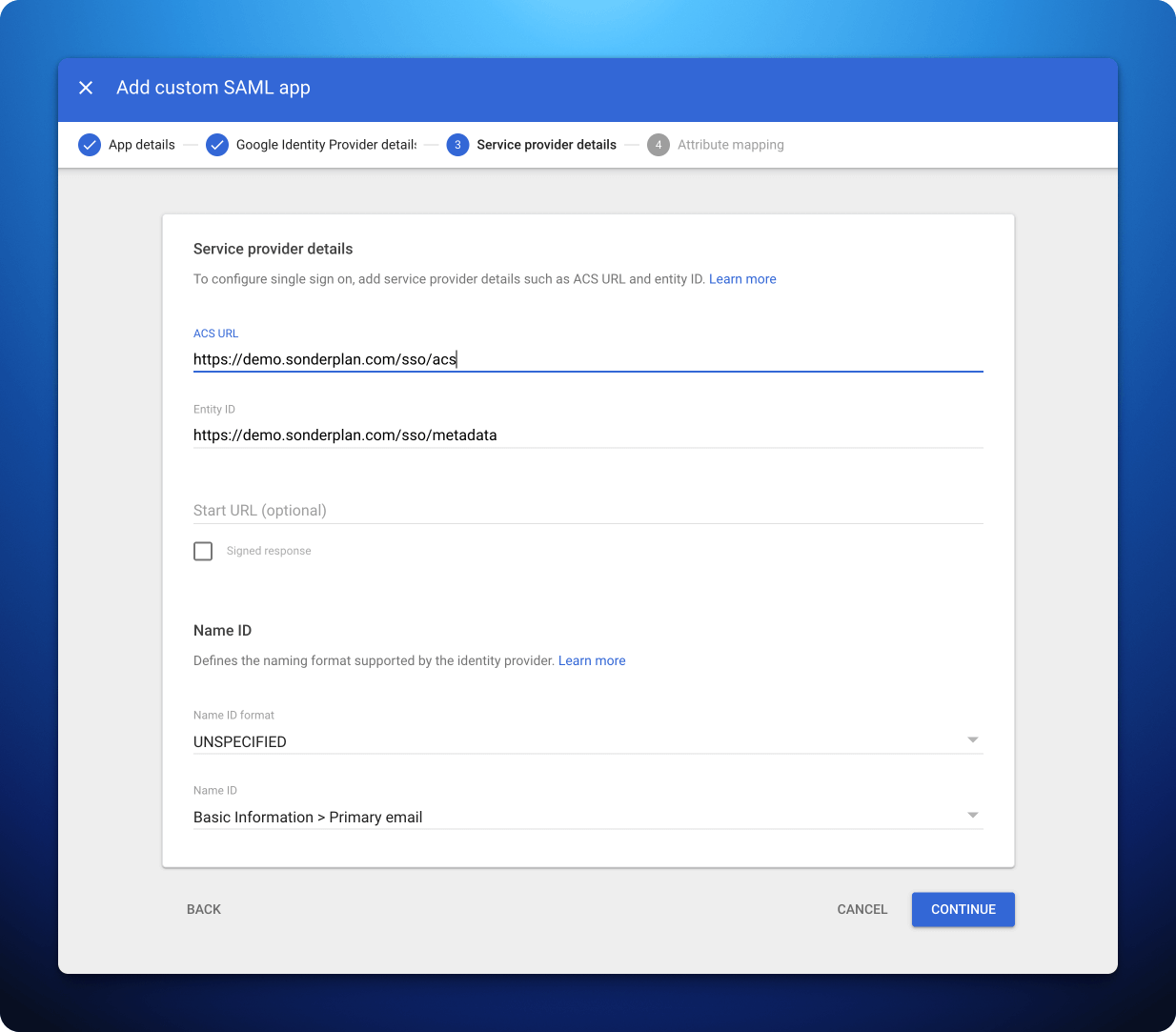
- Copy the Recipient / ACS (Consumer) URL from Sonderplan to -> ACS URL in Google Workspace Admin Console
- Copy the Entity ID / Audience / Metadata URL from Sonderplan to -> Entity ID in Google Workspace Admin Console
- Make sure Name ID in Google Workspace Admin Console is set to Basic information > Primary Email
- Click Continue
4. SAML attribute mapping for Google Workspace
4. SAML attribute mapping for Google Workspace
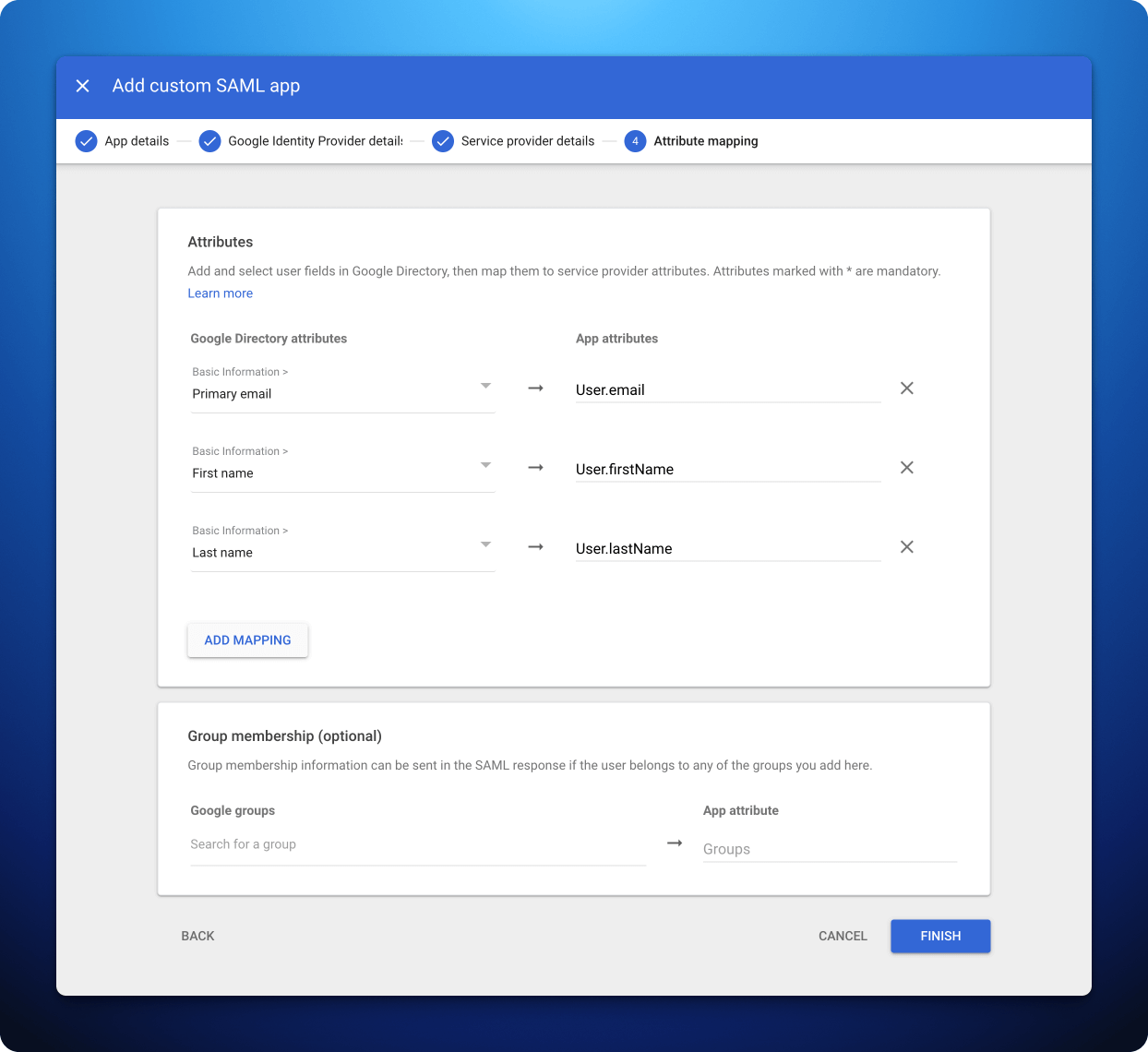
- Configure the mapping of Google Directory attributes to the attributes of Sonderplan. Please refer to the screenshot above or table below. | Google Directory attributes | App attributes | |------------------------------------|----------------| | Basic Information -> Primary email | User.email | | Basic Information -> First name | User.firstName | | Basic Information -> Last name | User.lastName |
- Click Finish
5. Enabling SAML for Google Workspace Users
5. Enabling SAML for Google Workspace Users
Once the app has been created, you’ll need to enable the SAML app for your Google Workspace users.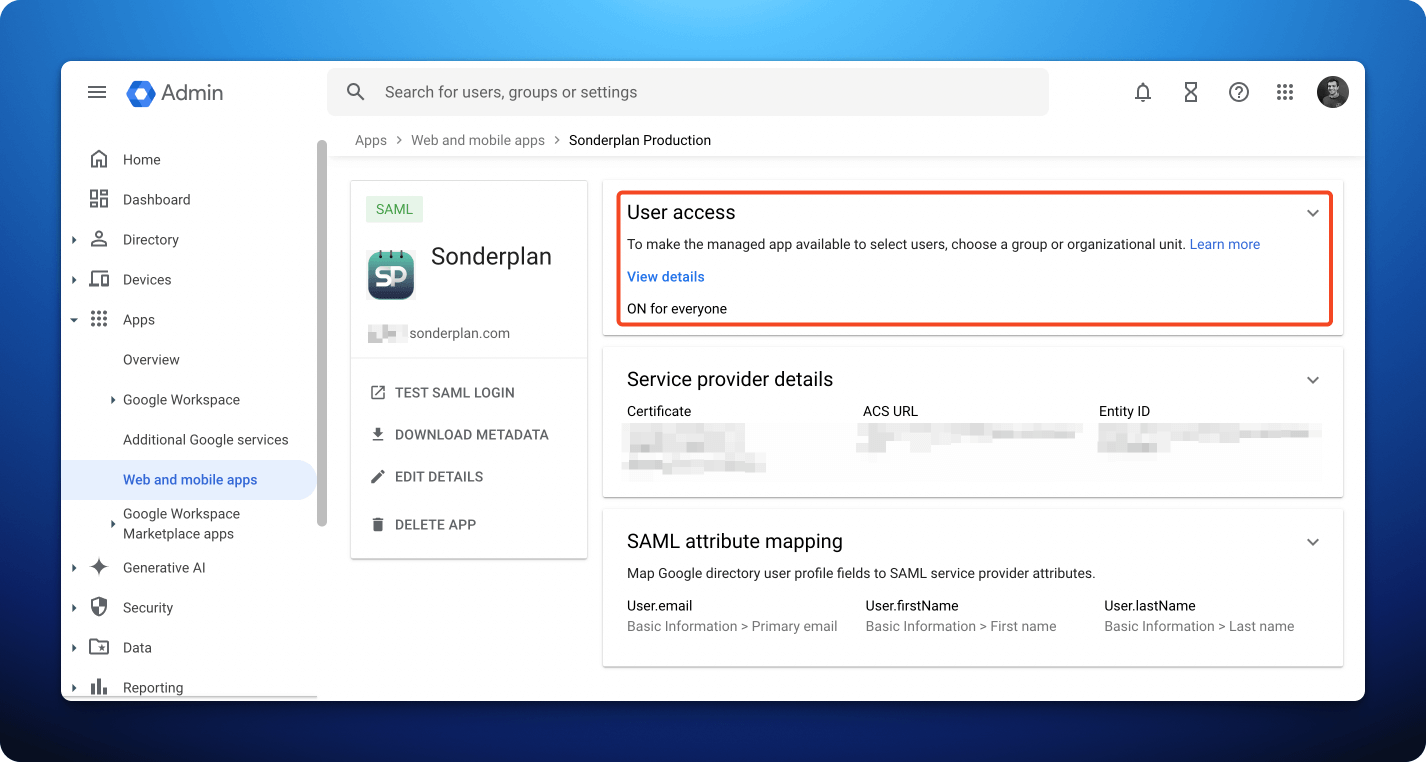

- In the Google Workspace Admin Console navigate to Apps -> Web and mobile apps -> Sonderplan -> User Access change the access setting to ON for everyone
- Finally, you’ll need to configure your users in Sonderplan for SSO
Microsoft Entra
To configure Sonderplan SAML SSO with Microsoft Entra, please expand and follow the instructions in each section:1. Create new Entra Enterprise Application
1. Create new Entra Enterprise Application
- Login to the Microsoft Azure Portal and navigate to your directory -> Enterprise Applications -> All applications -> New application

- In the Microsoft Entra Gallery, click Create your own Application
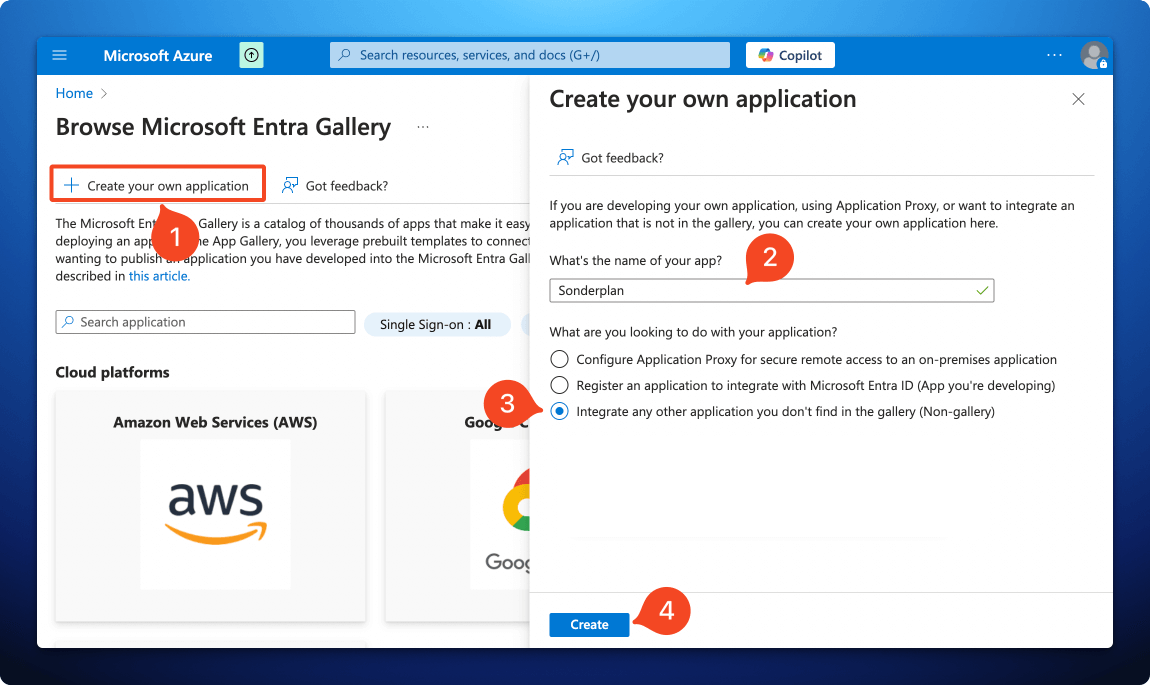
- Enter Sonderplan as the name of the app
- Check that the option Integrate any other application you don’t find in the gallery (Non-gallery) is selected
- Click Create
2. Enter Service Provider details into Entra
2. Enter Service Provider details into Entra
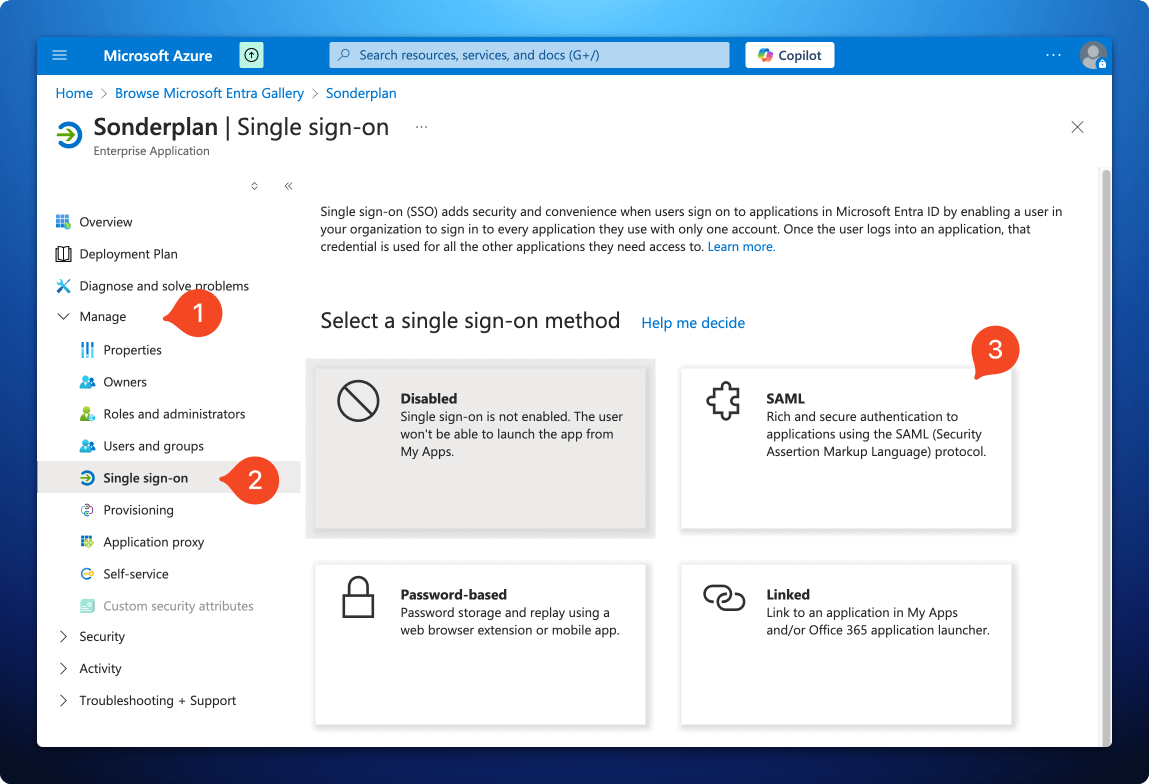
- In the newly created app Sonderplan app, expand the Manage section, then click Single sign-on -> SAML
- On the next screen, in the Basic SAML Configuration, click Edit
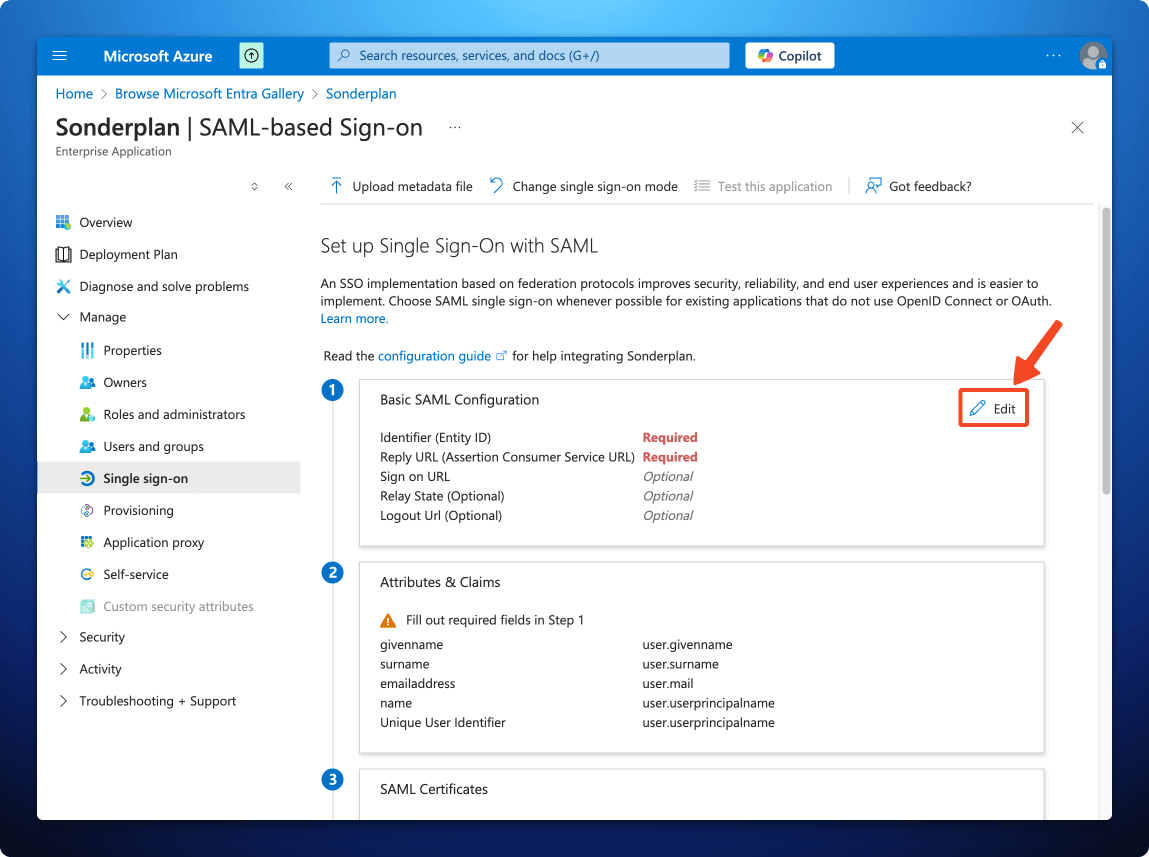
- In another window, open Sonderplan and head over to Admin -> System Settings and expand the SAML Single Sign On (SSO) settings panel
- Enable SAML SSO and enter Microsoft Entra as the Identity Provider Name then scroll down to the “2. Service Provider Details (Sonderplan)” section
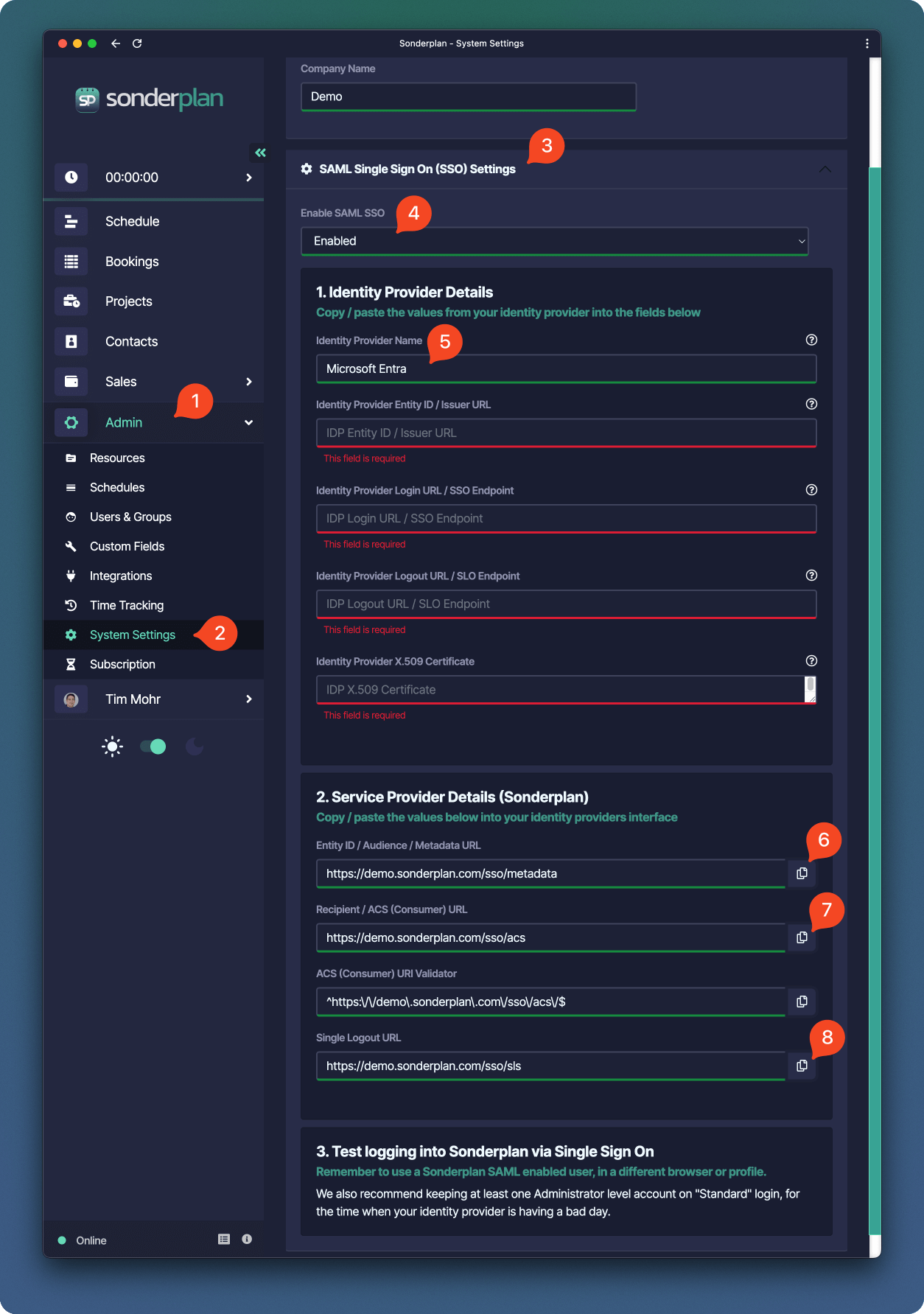
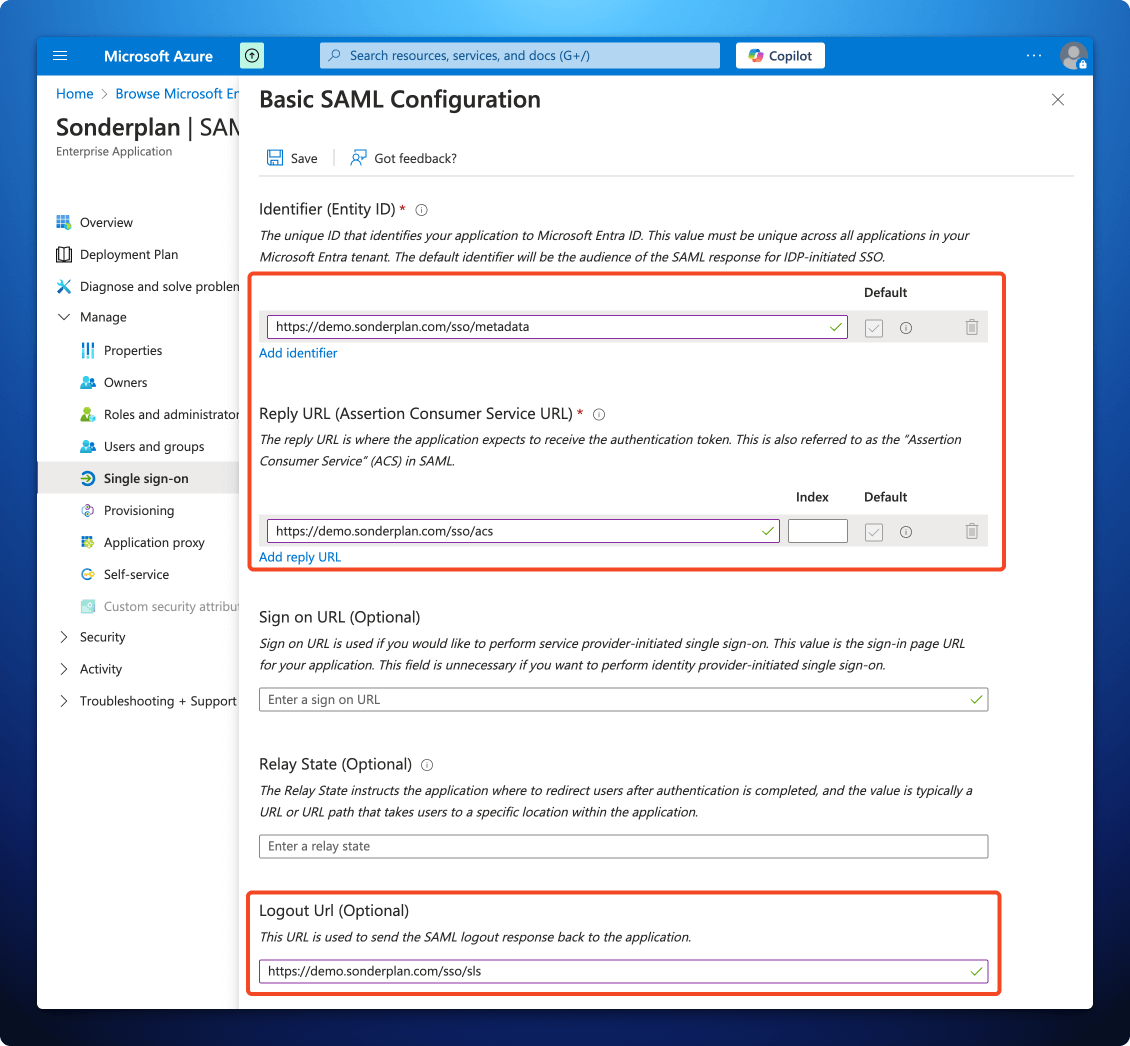
- Copy the Entity ID / Audience / Metadata URL from Sonderplan to -> Identifier Entity ID in the Azure SAML configuration
- Copy the Recipient / ACS (Consumer) URL from Sonderplan to -> Reply URL (Assertion Consumer URL) in the Azure SAML configuration
- Copy the Single Logout URL from Sonderplan to -> **Logout Url (Optional) in the Azure SAML configuration
- Finally click Save at the top of the Basic SAML Configuration screen in the Azure Portal, then click the x in the top right corner
3. Copy Entra details into Sonderplan
3. Copy Entra details into Sonderplan
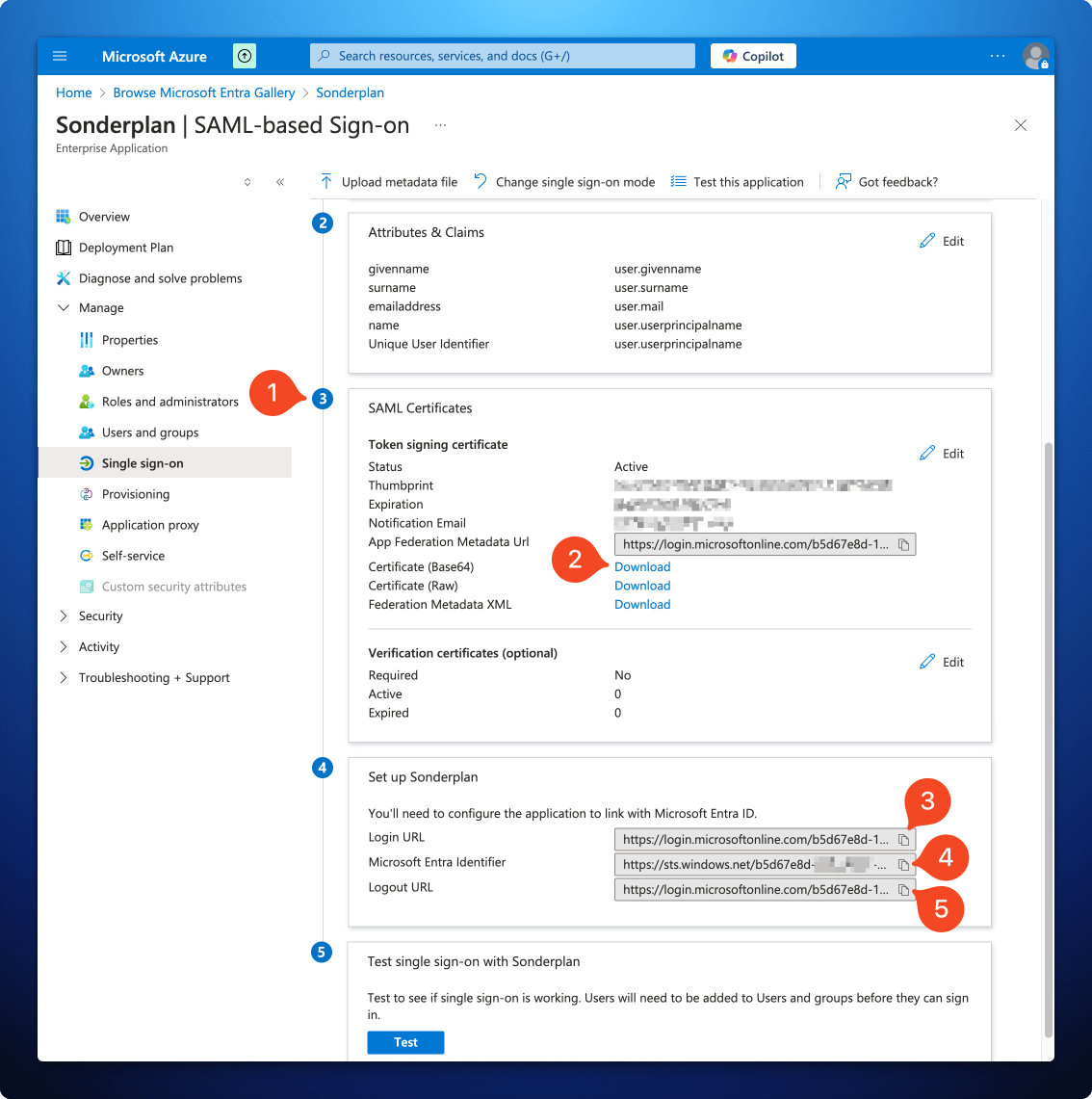
- Still in the Azure Portal, but back on the SAML-based Sign-on page for the Sonderplan Enterprise app, scroll down to section 3 SAML Certificates
- Download the Certificate (Base64), open the Sonderplan.cer file in a text editor on your computer and copy the entire contents of the file into the Identity Provider X.509 Certificate in the Sonderplan SAML SSO settings textarea
- Copy the Login URL from the Azure Portal to -> Identity Provider Login URL / SSO Endpoint in Sonderplan
- Copy the Microsoft Entra Identifier from the Azure Portal to -> Identity Provider Entity ID / Issuer URL in Sonderplan
- Copy the Logout URL from the Azure Portal to -> Identity Provider Logout URL / SLO Endpoint in Sonderplan
- Click Save Changes in the top right corner of Sonderplan

4. SAML Attribute Mapping for Entra
4. SAML Attribute Mapping for Entra
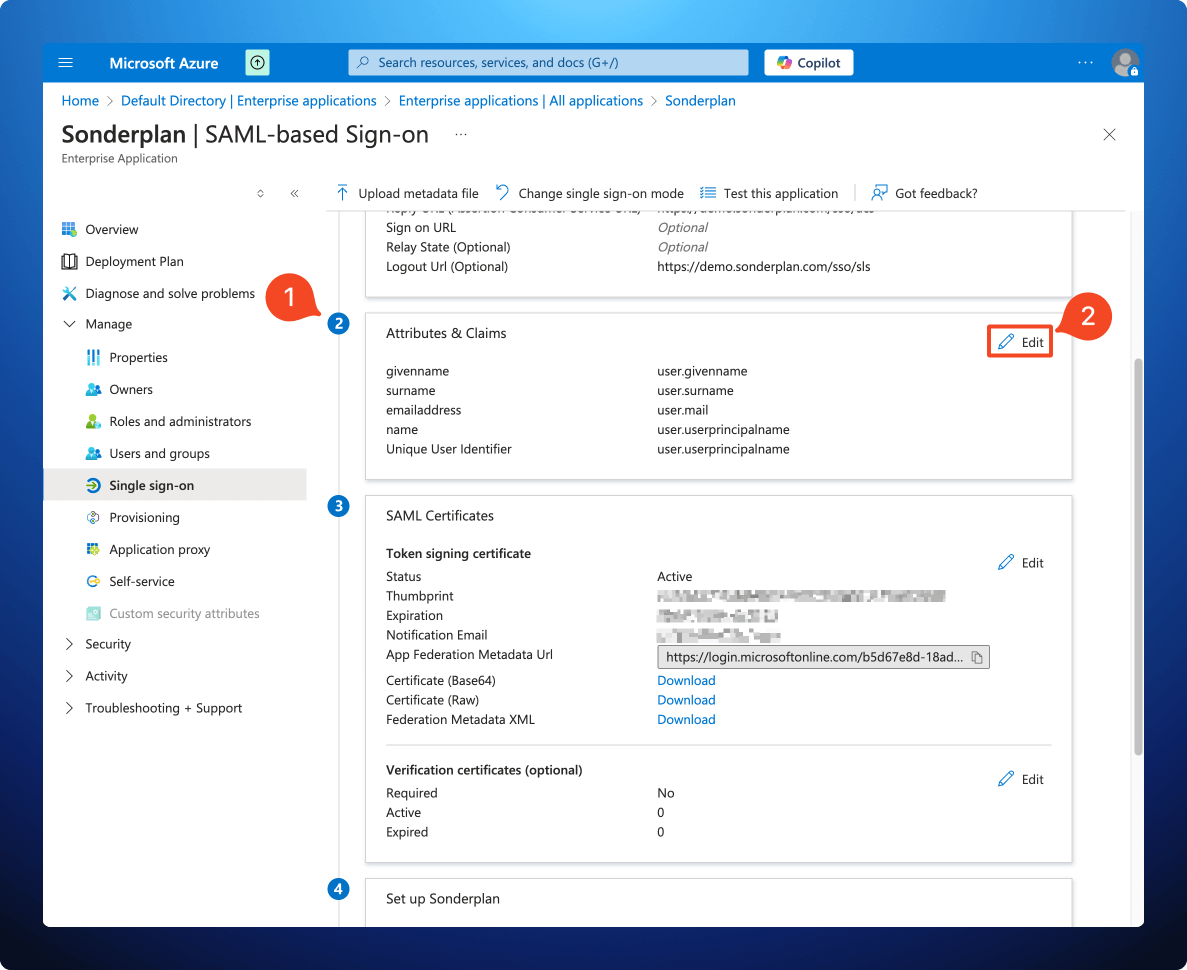
- Still in the Azure Portal, but back on the SAML-based Sign-on page for the Sonderplan Enterprise app, scroll down to section 2 Attributes & Claims and click Edit
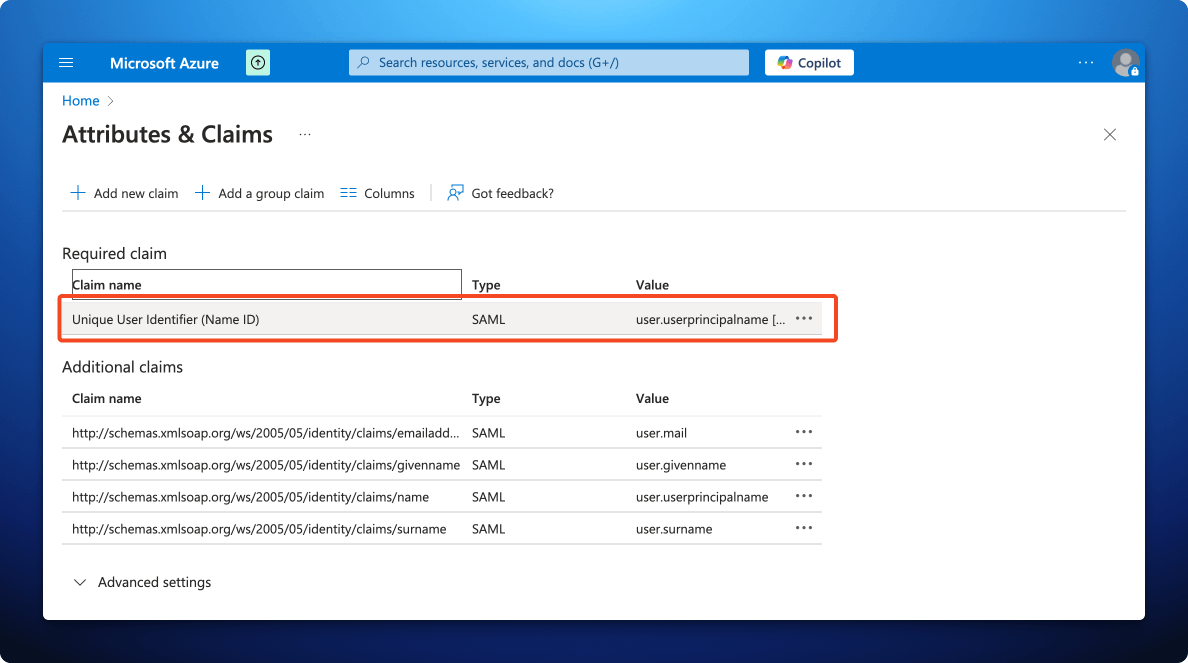
- In the Attributes & Claims screen, click the Unique User Identifier (Name ID) claim
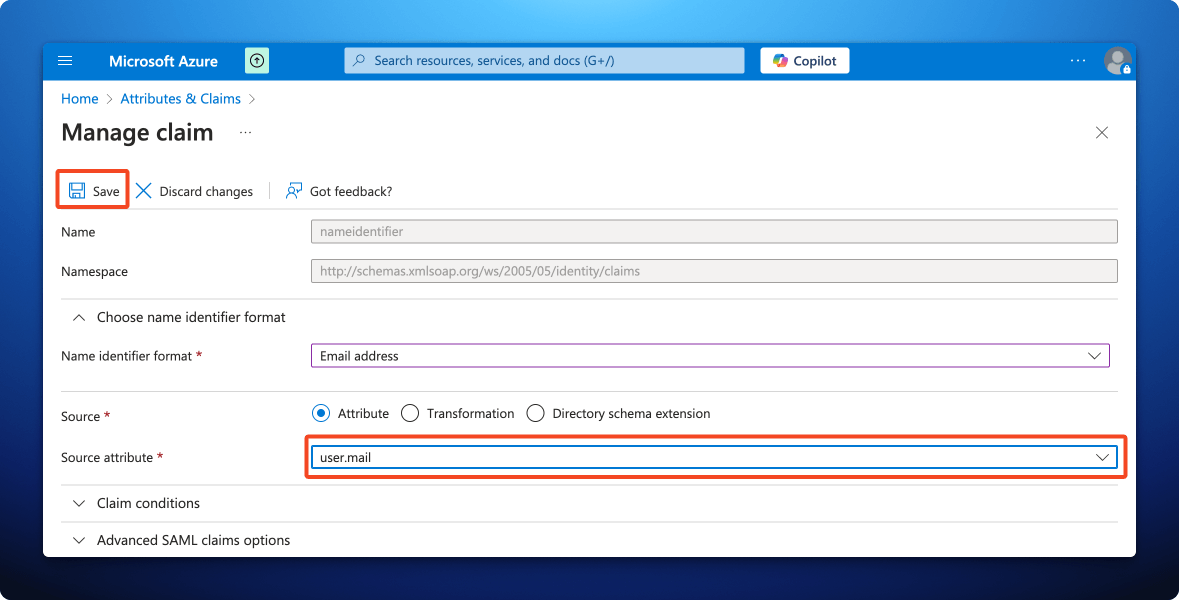
- Change the Source Attribute to user.mail and click Save
5. Finalise Sonderplan Entra Enterprise Application
5. Finalise Sonderplan Entra Enterprise Application
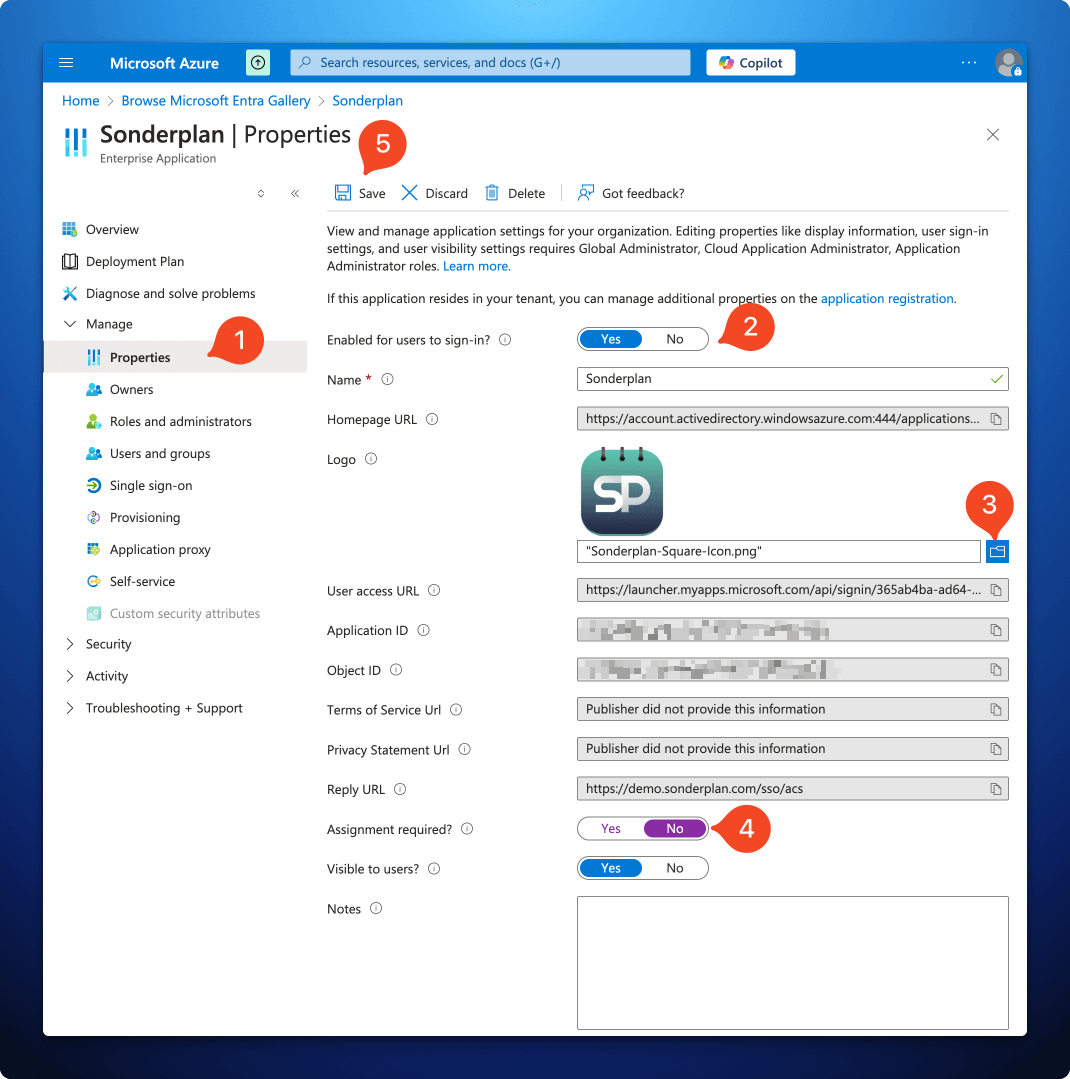
- Still in the Sonderplan Enterprise application, expand the Manage section, then click on Properties
- Ensure the Enabled for users to sign-in? slider is set to Yes
- Upload the App Icon to the Logo field, which you can save from here:

- Change Assignment required? slider to No
- Click Save in the top left corner
- Finally, you’ll need to configure your users in Sonderplan for SSO
Okta
To configure Sonderplan SAML SSO with Okta, please expand and follow the instructions in each section:1. Create new Okta SAML App
1. Create new Okta SAML App
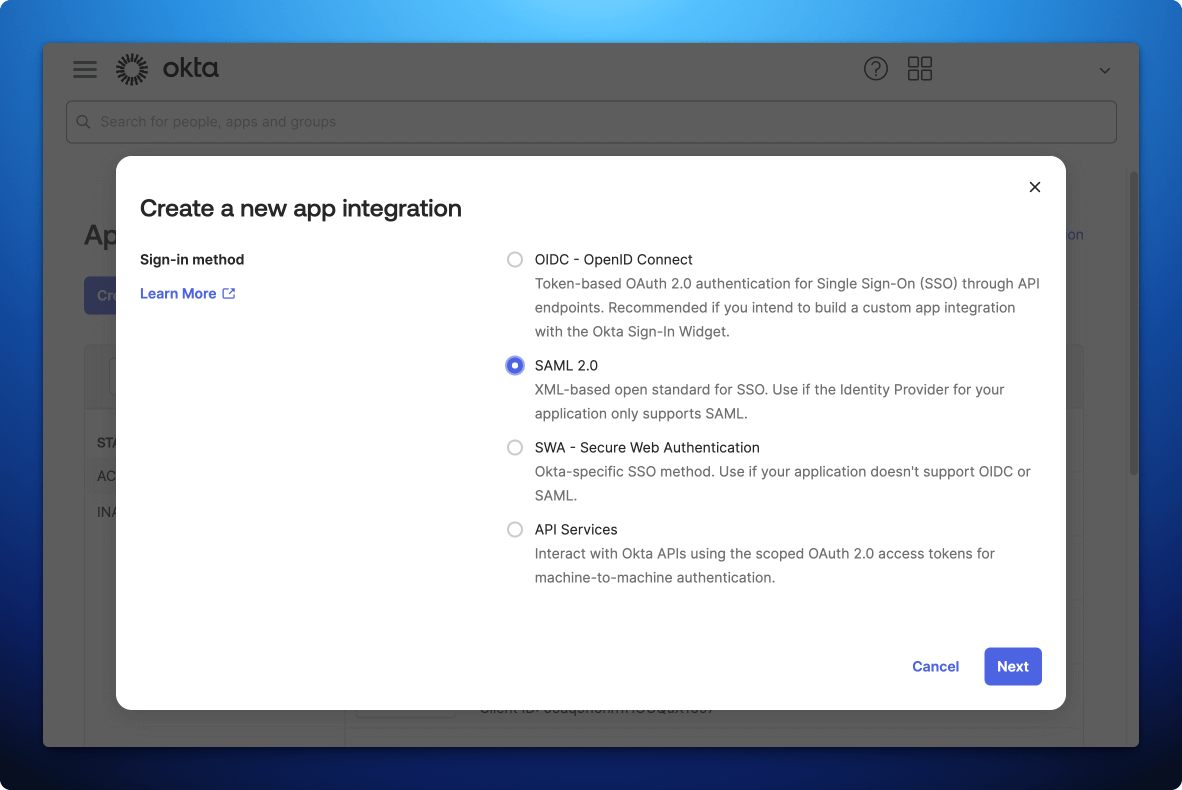
- In the Okta Admin Console, go to Applications -> Applications
- Click Create App Integration
- Select SAML 2.0 as the Sign-in method, then click Next
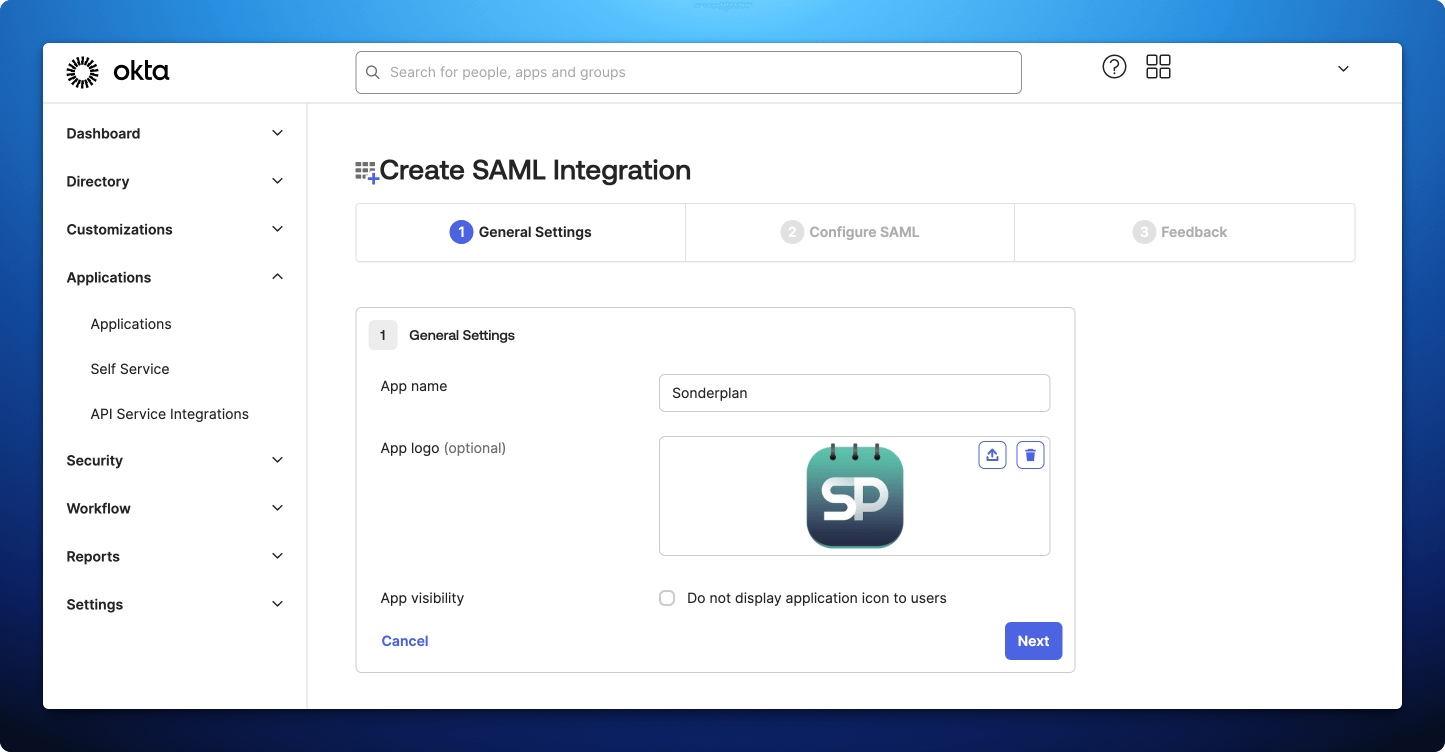
- Enter Sonderplan as the App Name
- Upload the App Icon to the Logo field, which you can save from here:

- Then click Next
2. Enter Service Provider details into Okta
2. Enter Service Provider details into Okta
- In Sonderplan, head over to Admin -> System Settings and expand the SAML Single Sign On (SSO) settings panel
- Enable SAML SSO and enter Okta as the Identity Provider Name
- Leave the remaining fields blank for now, and scroll to the section titled 2. Service Provider Details (Sonderplan)

- Copy the Recipient / ACS (Consumer) URL from Sonderplan to -> Single sign-on URL in Okta Admin
- Copy the Entity ID / Audience / Metadata URL from Sonderplan to -> Audience URI (SP Entity ID) in Okta Admin
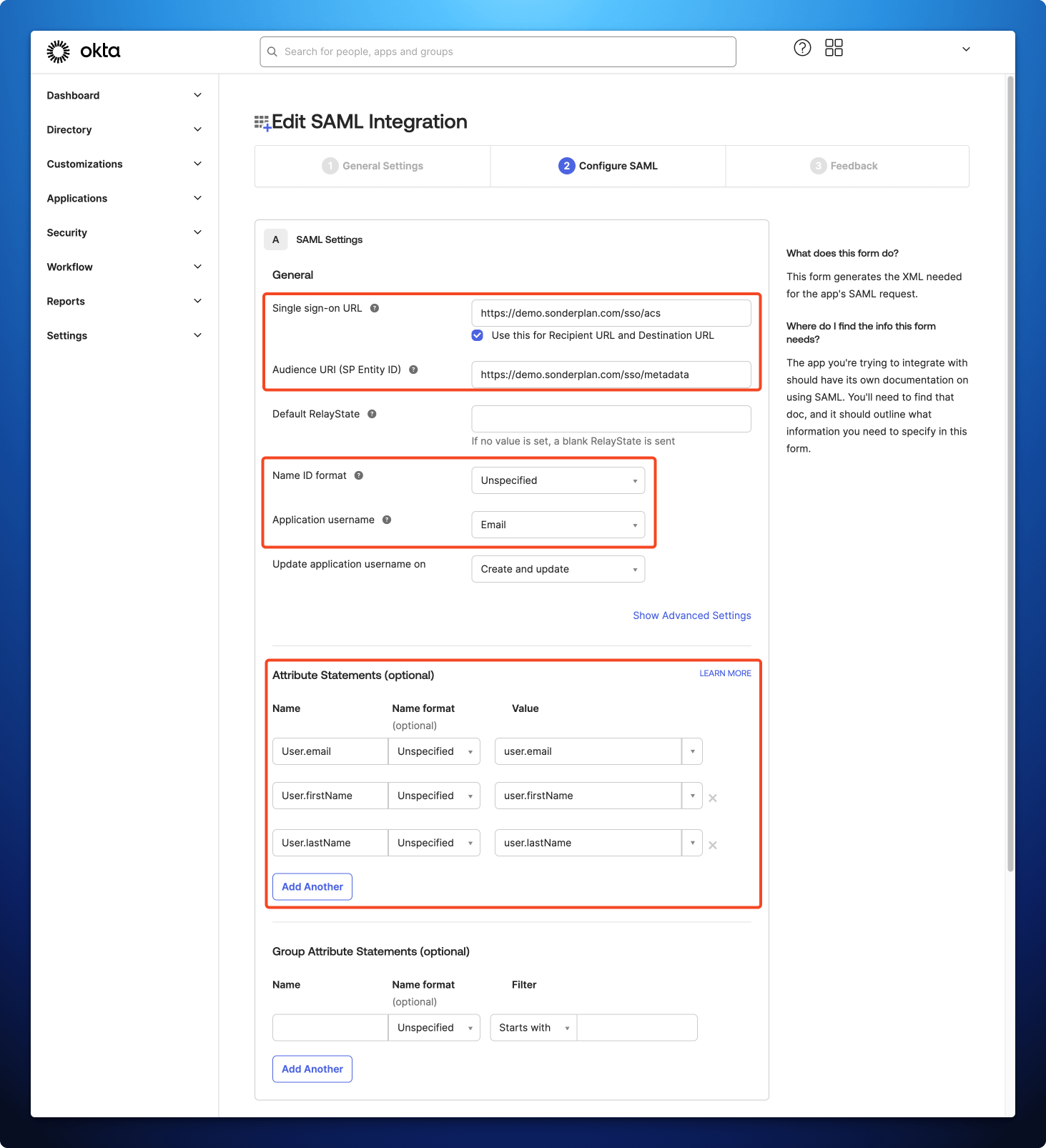
- Make sure Name ID format in Okta Admin is set to Unspecified
- Set Application username in Okta admin to Email
- In the Attribute Statements (Optional) section, define the following mapping:
| Name | Name format | Value |
|---|---|---|
| User.email | Unspecified | user.email |
| User.firstName | Unspecified | user.firstName |
| User.lastName | Unspecified | user.lastName |
- Click Next
- Select I’m an Okta customer adding an internal app
- Check This is an internal app that we have created
- Click Finish
3. Enter Okta details into Sonderplan
3. Enter Okta details into Sonderplan
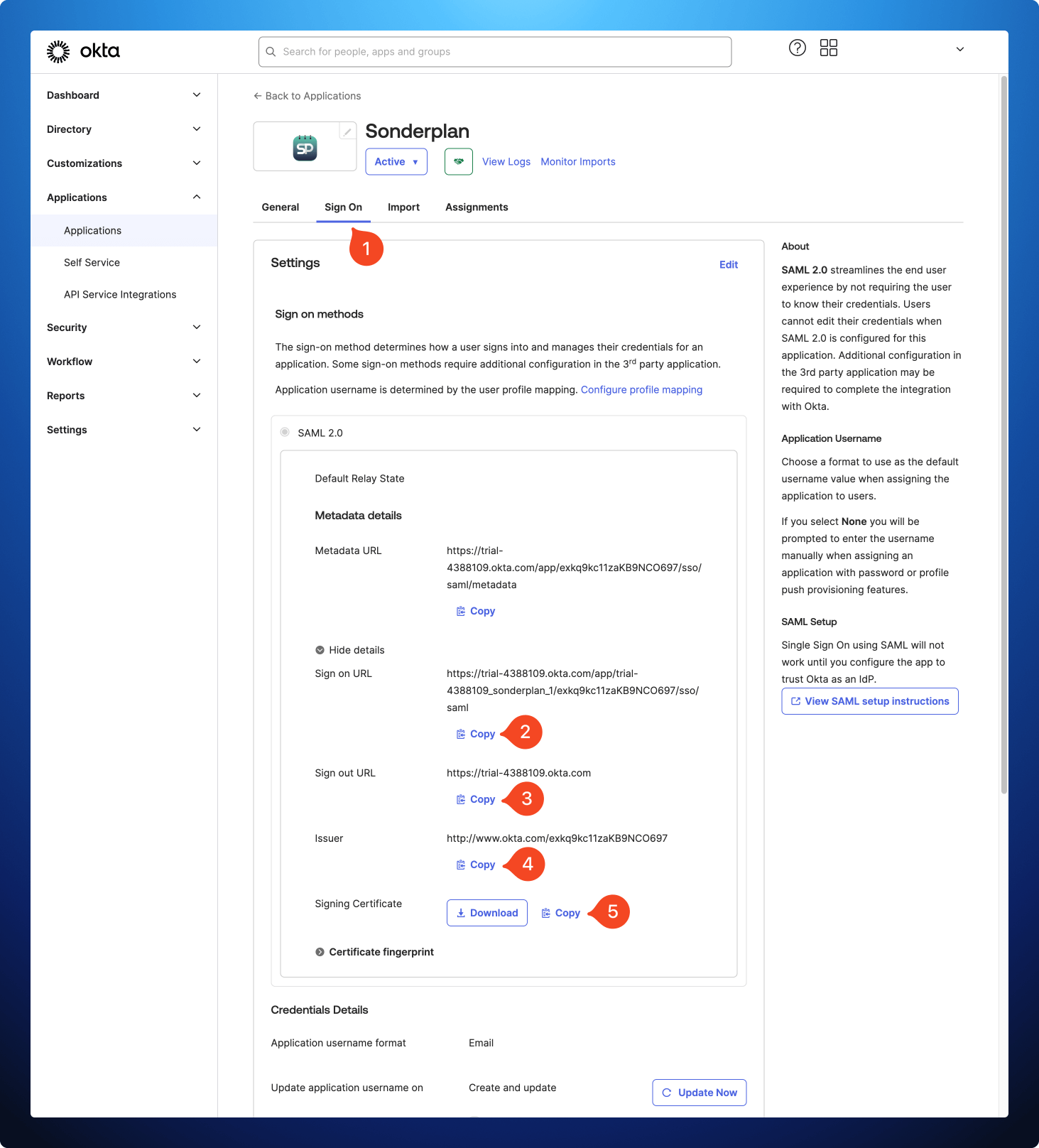
- In the Okta Admin panel, click Sign On within the Sonderplan* application and scroll down to the SAML 2.0 section
- Copy the Sign on URL from Okta to -> Identity Provider Login URL / SSO Endpoint in Sonderplan
- Copy the Sign out URL from Okta to -> Identity Provider Logout URL / SLO Endpoint in Sonderplan
- Copy the Issuer from Okta to -> Identity Provider Entity ID / Issuer URL in Sonderplan
- Copy the Signing Certificate from Okta to -> Identity Provider X.509 Certificate in Sonderplan
- Click Save Changes in the top right corner of Sonderplan
- Finally, you’ll need to configure your users in Sonderplan for SSO
Configure Users for SSO
Once you’ve correctly configured SAML, you’ll need to enable SAML SSO Login for each of your users in Admin -> Users & Groups -> User Editor -> SAML SSO Login.To prevent accidental account lockouts due to potential misconfiguration or Identity Provider outages, we recommend maintaining at least one Super Administrator account configured with the Standard Login method.